On this page
Exercise 05: Password Guessing
At this point you should have a list of valid member email addresses. We'll use these to perform a dictionary attack against the member login and attempt to gain access to other member accounts.
Again, we will use Burp Intruder for this!
Building a List of Passwords
Once again our earlier recon will come in handy here. We will be performing an online password guessing attack, meaning we will send one HTTP request for each password we want to attempt against an account.
In order to decrease the risk of account lockouts, and increase our chances of success, we should look to refine our password list as much as possible and send the lowest number of HTTP requests we can (which also decreases the risk of denial of service or being detected).
Password Policies
Did you notice when registering a member account that there was a minimum length requirement for the password?
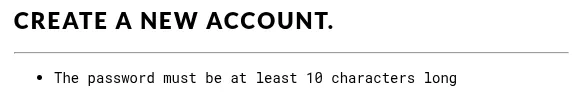
It is a fair assumption that most members will have passwords that are 10 characters or more in length, so it's less likely we'll get a hit with passwords shorter than that (not impossible though).
SecLists is a great resource for password lists for different types of systems and applications. For this exercise, I have taken this list: 2024-197_most_used_passwords.txt. It contains 197 commonly used passwords, but if we get rid of everything less than 10 characters long we can narrow it down to 17 passwords.
If you know more about the password policy for a system, you may be able to reduce your list further. For example, if the policy requires uppercase characters, you could remove those with only lowercase or numbers.
Consider This 💡
If we hadn't done our recon and user enumeration in the previous exercises, and refinement of our password list, we'd be looking at potentially trying 197 passwords against 20 different member emails (some non-existant, and therefore pointless to try). That'd be a total of 3940 HTTP requests.
However, after performing user enumeration, we have narrowed our search down to 6 valid member emails. And with just 17 passwords, we are now looking at sending 102 HTTP requests, a significant reduction.
Now we have a higher chance of success and a lower risk of account lockouts, denial of service, or being detected 😎.
Password Guessing with Burp Intruder
Once again, send the POST request to /login to Intruder (hopefully you
know how to do this by now).
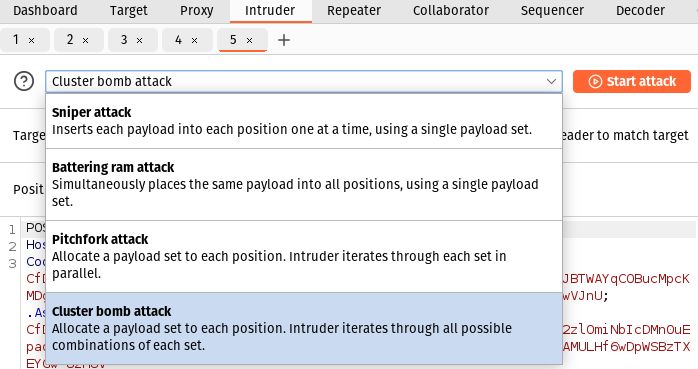
This time, set the attack type to Cluster bomb attack by clicking on the drop-down menu above the request editor:
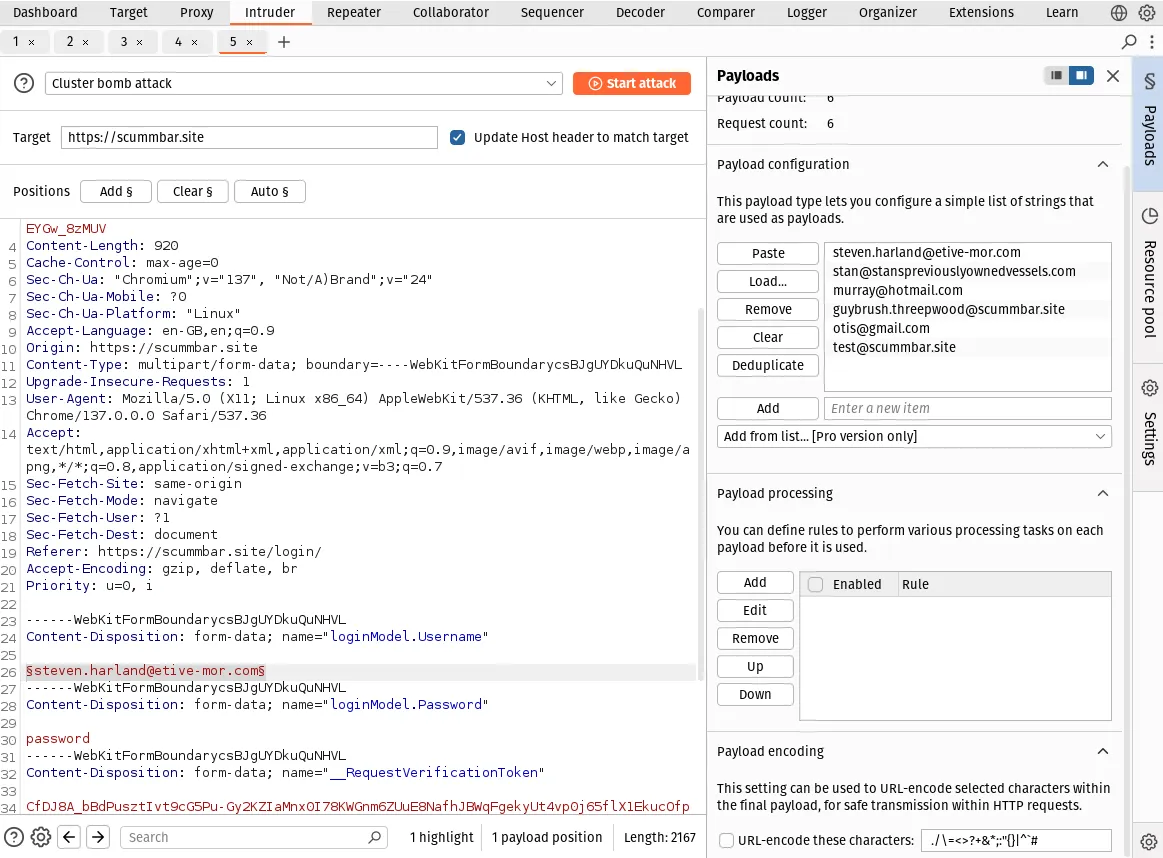
Highlight the email address in the request body, and click the button labelled
Add § to add a placeholder. Under Payload configuration, paste in your
list of valid email addresses to test.
Again, under Payload encoding, un-check the box labelled
URL-encode these characters (this is to prevent the . character in email
addresses being encoded and giving us incorrect results):
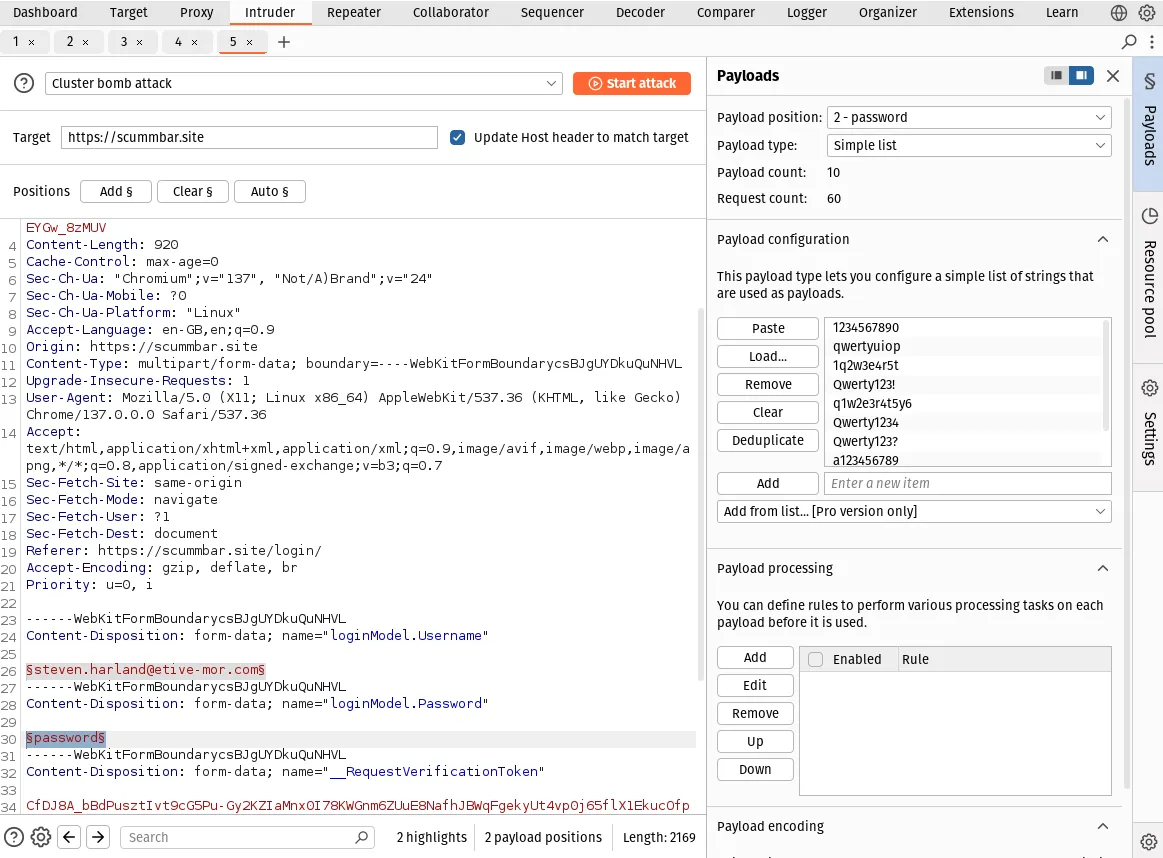
Do the same with the password field in the request body. We have provided a list of passwords for you to use (this is an even smaller list of just 10 passwords to save some time in the live workshop):
Click the Start attack button. A new window should pop up and Burp will start sending requests for every combination of payloads in the given lists (this is the cluster bomb attack):
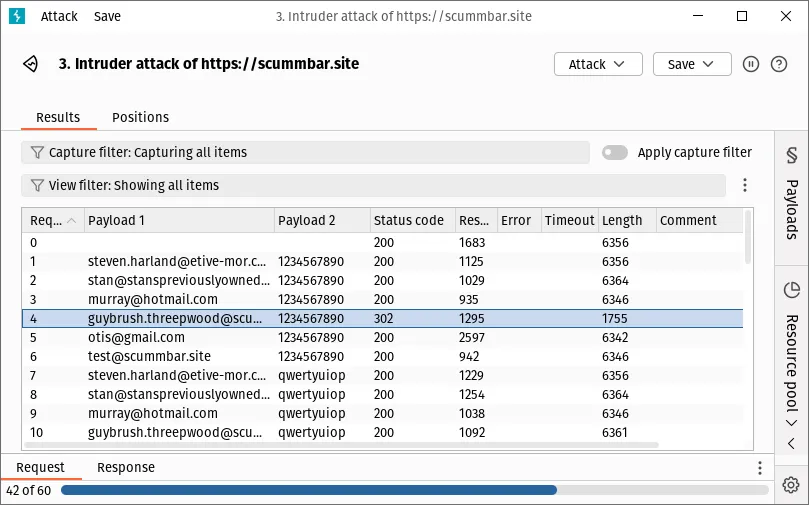
Watch out for differences in response status code, content length, or timing which may indicate whether a given email and password is valid. Try logging in with any credentials you find to verify them.