On this page
Exercise 04: User Enumeration
In this exercise we'll look at user enumeration vulnerabilities and how to leverage it to determine which members exist in the database from a list of email addresses.
Testing for User Enumeration
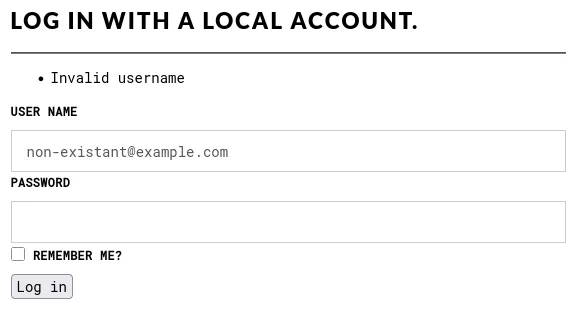
Browse to the login page of the website and enter an email address that is likely to be invalid. Note that error message we get back says Invalid username:
Now, enter the email address for the account you registered earlier, but using an incorrect password. Notice how the error message now says Invalid password:
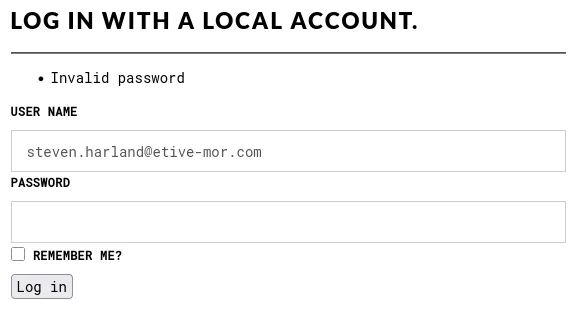
We now know that when the application responds with "Invalid password" the email we provided is valid (even though the password is not).
Error messages aren't the only difference you should look out for. Consider also:
- HTTP response status codes.
- Response content length.
- Length of time taken to respond.
Noticeable differences in any of these values could indicate whether a user exists or not.
Building a List of Emails
In the previous exercise on passive recon we looked at the reviews API and how it returned member email addresses in responses. If we look around a few of the product pages we can start building up a list of likely members:
steven.harland@etive-mor.com
stan@stanspreviouslyownedvessels.com
murray@hotmail.com
guybrush.threepwood
otis@gmail.com
Also notice that the website has an email address in the footer (info@scummbar.site):
![]()
Based on this email, and the names we found on the People page, we
can add to our list of likely email addresses. We may not know the exact name
format, but we can try a few typical combinations of first/last name. We can
also add common things like admin or test. For example:
guybrush@scummbar.site
g.threepwood@scummbar.site
guybrush.threepwood@scummbar.site
threepwood.g@scummbar.site
admin@scummbar.site
administrator@scummbar.site
test@scummbar.site
Put together a list of potential member email addresses, or use the list we have provided here: emails.txt.
User Enumeration with Burp Intruder
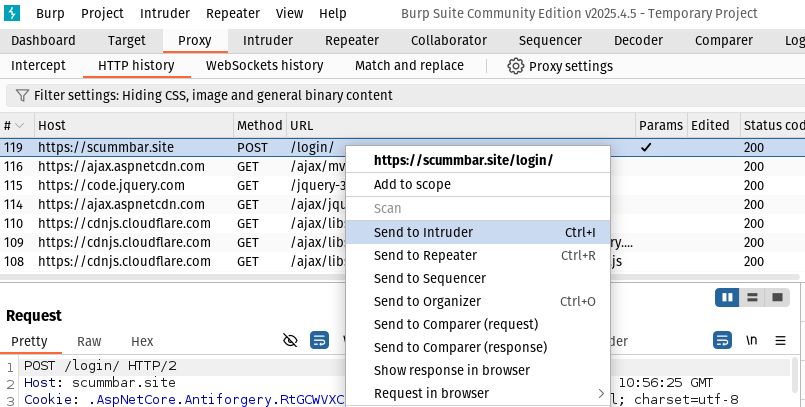
Head back to the Proxy > HTTP History tab in Burp. Find the POST request to
/login and send it to Intruder:
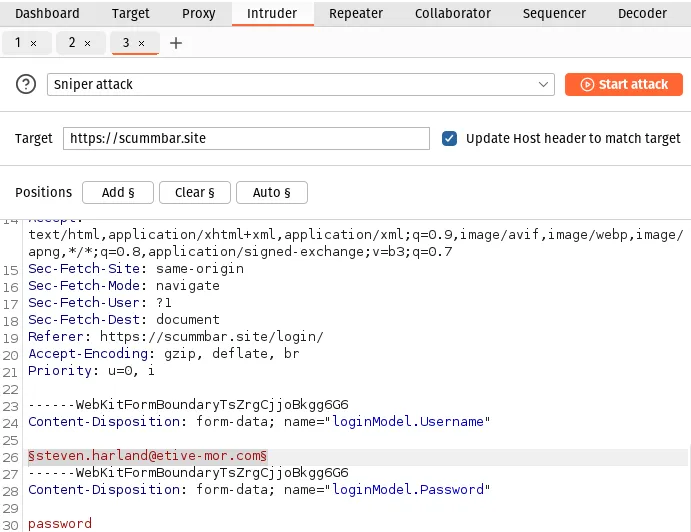
Go to the Intruder tab, highlight the email address in the request body, and click the button labelled Add § to add a placeholder.
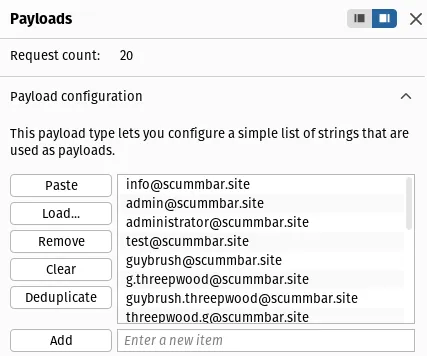
Under Payload configuration, paste in your list of email addresses to test:
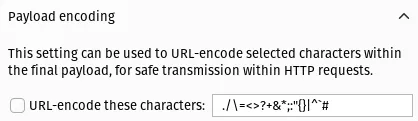
And under Payload encoding, un-check the box labelled
URL-encode these characters (this is to prevent the . character in email
addresses being encoded and giving us incorrect results):
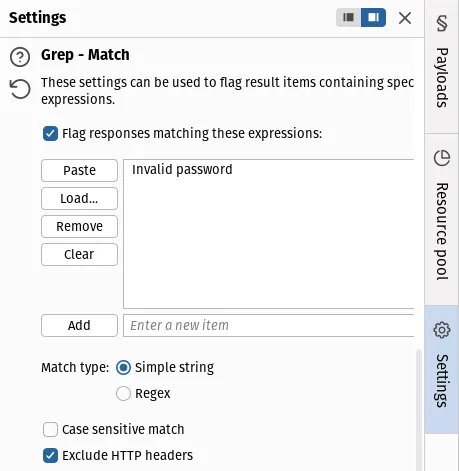
Go to the Intruder Settings tab (on the right of the window by default),
and under Grep - Match click the Clear button, and Add the string
Invalid password. Also make sure
Flag responses matching these expressions is checked:
Click the Start attack button. A new window should pop up and Burp will start sending requests for each email in the list:
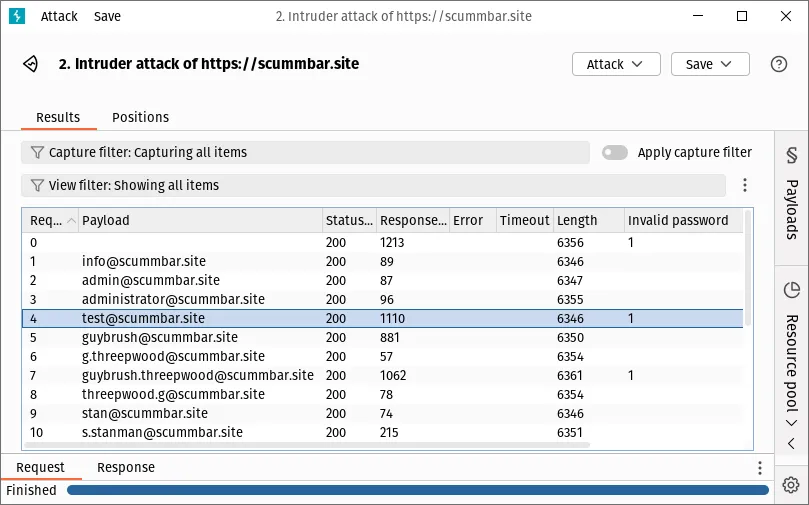
The responses containing the text Invalid password will be flagged - these
email addresses are therefore valid member usernames. Create a new text file
with just these email addresses inside of it - we will use this for password
guessing in the next exercise.
Resources
- List for user enumeration attack
- Burp Intruder documentation
- CrossLinked (a tool for scraping employee names from LinkedIn)