Exercise 02: Active Recon
Now we enter the danger zone 🚨.
Active recon typically involves running automated tools which can make hundreds or thousands of requests to the target application.
Be wary of using these techniques on production sites. Use a dev or test environment if you can and monitor your target as you scan to ensure you aren't causing performance issues.
Dirbusting with Burp Intruder
Dirbusting (directory busting) is a technique used to discover hidden pages, API endpoints, exposed configuration files, database backups, and so on. We'll use the Burp Intruder tool for this.
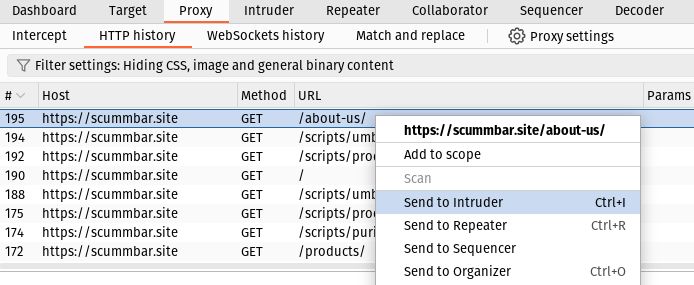
First, select a request in the Proxy > HTTP history tab, right-click it and select Send to Intruder (or alternatively, press Ctrl+I on your keyboard):
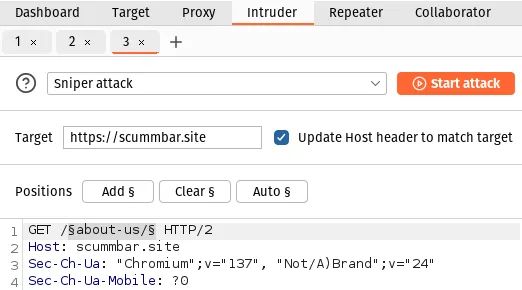
Next, go to the Intruder tab and you should see the request on the left. Highlight the URL path, excluding the first forward slash, and click the button labelled Add § to add a placeholder:
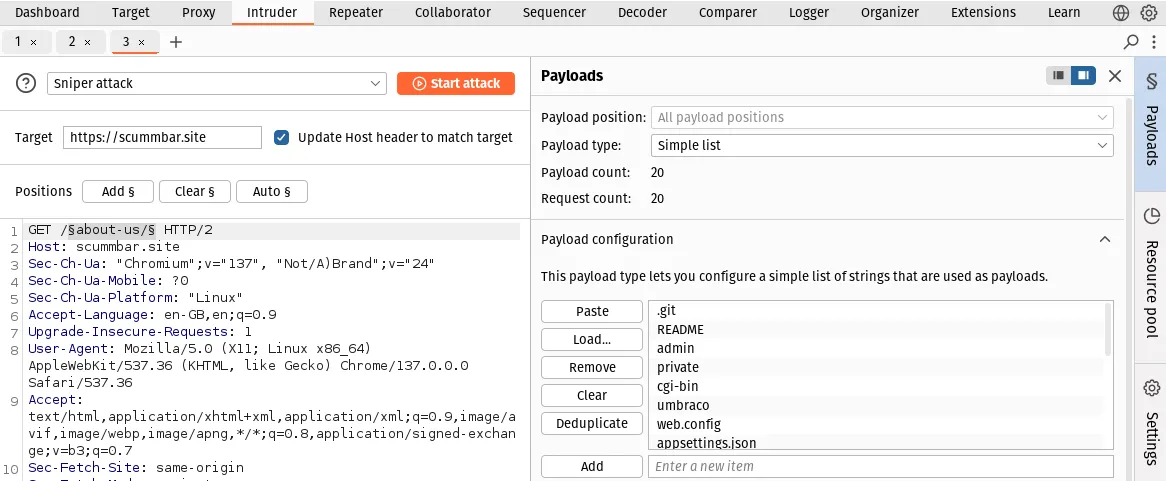
On the right, under Payload configuration, paste in a list of strings to test (you can use the list directories.txt):
We've provided a minimal list for this demo so that the attack will finish quickly. However, on a real pentest you may want to use bigger lists such as those available in the SecLists GitHub repo.
Click the Start attack button. A new window should pop up and Burp will start sending requests for each item in the list:
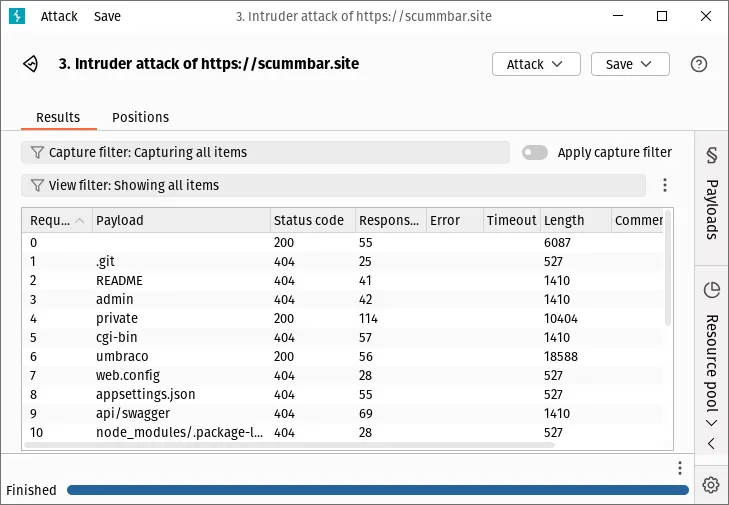
Filter the results to hide the 404s, and we should be left with some URLs of interest - explore them!
Run the same attack on any other subdomains you discovered in the previous exercise - can you spot any differences between the dev and production sites?
Vulnerability Scanning with Nuclei
Now we'll head back to the terminal and look at running a basic vulnerability scan. Vulnerability scanners attempt to find known vulnerabilities, misconfigurations and potentially interesting files.
Enter the following command to run a default Nuclei scan and save the output to file:
nuclei -u https://scummbar.site/ -o scummbar.txt
Review the results and see what else you can learn about the target from them. Be on the lookout for false positive results, and investigate them.
We won't review every finding from the scan. It will mostly be informational issues such as missing HTTP headers and such. Vuln scanning is good for identifying low-hanging fruit, but a vulnerability scan is not a pentest, so let's move on.