On this page
Exercise 01: Passive Recon
In this exercise we will look at some simple techniques for passive recon of the target application.
The aim of passive recon is to be stealthy and not alert the website owner that we are attacking it.
Analysing Web Traffic with Burp Proxy
Burp Proxy allows us to intercept and inspect the underlying HTTP requests and responses transmitted between our browser and the target web server.
First launch Burp Suite. You can find it under the Web Application Analysis category in the Kali applications menu, or your Windows Start Menu. You may get a warning about your installed Java version, but this can usually be ignored.
Proceed with a temporary project and the default Burp configuration:
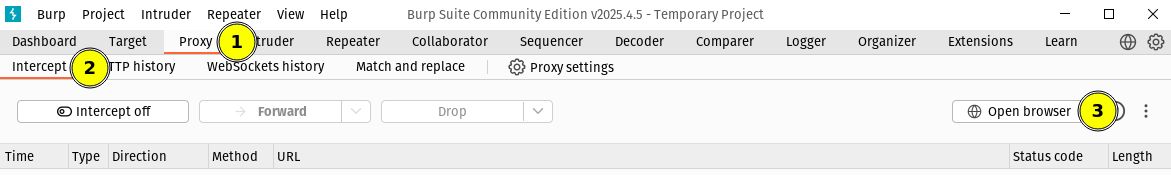
Go to the Proxy > Intercept tab and click the Open Browser button:
This will launch the Chromium browser that is bundled with Burp Suite and is preconfigured to proxy requests through it. You can also use an external browser, but you will need to configure it to proxy through Burp (for example, see Configuring Firefox to work with Burp Suite).
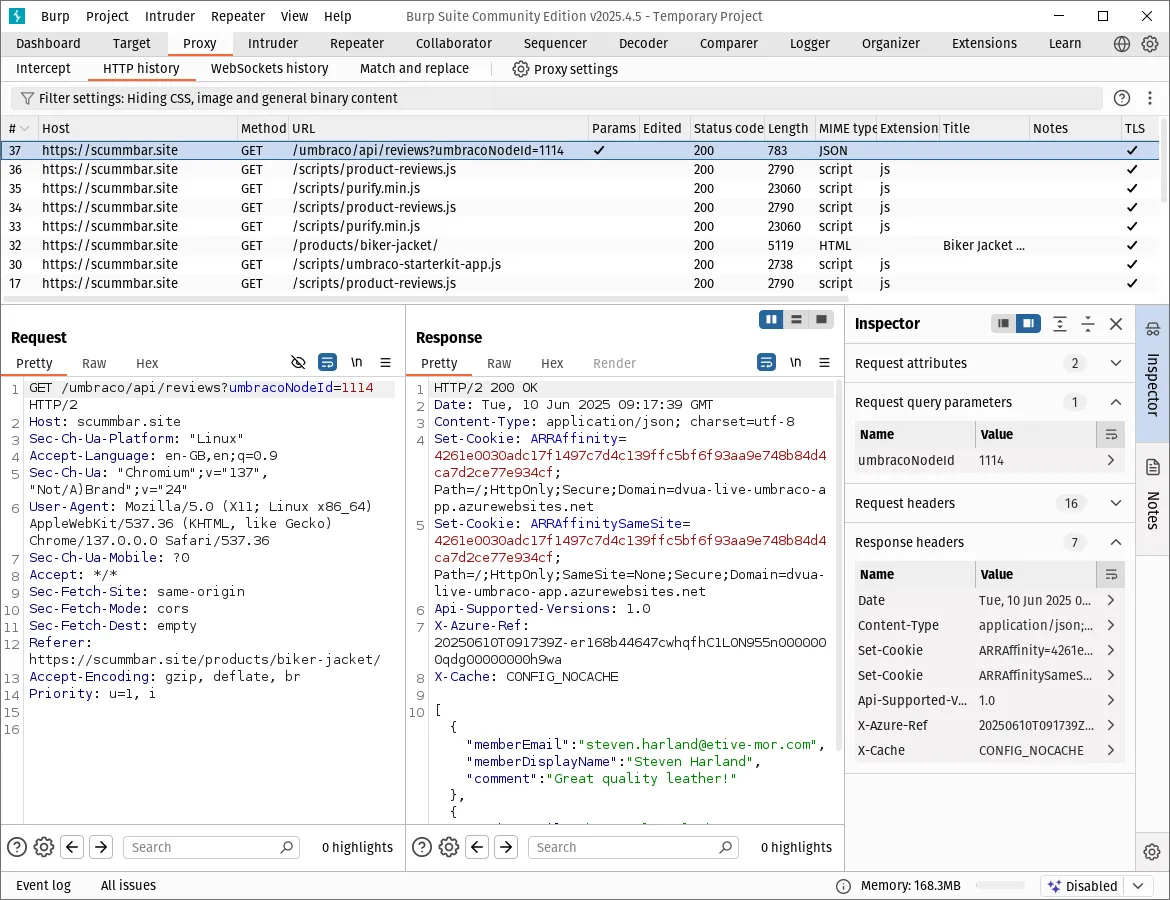
Browse to the target site again in Burp's browser and navigate around a bit. Then head back to Burp and select the Proxy > HTTP History tab. You should see all the requests for the pages you just visited. Click on any request to view the raw HTTP request and subsequent response from the server:
Some things you to look out for at this stage:
- Interesting features or functionality that we might want to attack later on.
- Think web forms, API endpoints, etc.
- Names and email addressses of potential users/members.
- Companies often have "People" pages on their websites.
- Interesting HTTP headers (both in the requests and responses).
- HTML and JavaScript code (and code comments).
- Web frameworks/packages used, including version numbers.
Product Reviews API Information Disclosure
As you were browsing around the site, you may have noticed that there is an API that returns member reviews for a given product. This API leaks some information in its response that isn't displayed on the site. Can you spot what it is?
Subdomain Enumeration with Sublist3r
Subdomain enumeration is the process of finding valid subdomains for a given domain. This is a great way to discover dev or staging deployments, admin panels, or other related applications.
We'll use the sublist3r command-line tool for this. Sublist3r queries a
number of third-party services to discover subdomains such as DNS (Domain Name
System), Google, and Bing. Although this is an automated scanner, we consider
it a passive technique because it does not make requests to the target
application itself.
Open a terminal in Kali and enter the following command:
sublist3r -d scummbar.site
Keep a note of any subdomains you find. We'll scan them in the next exercise on active recon!
Resources
- Burp Proxy documentation
- Sublist3r GitHub repo
- Subfinder (alternative to Sublist3r)
- OWASP Amass (does subdomain enumeration and more)